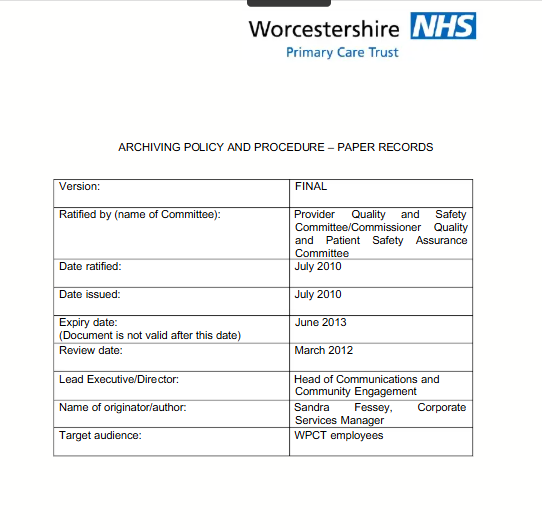
Archiving Policy
| Institution | University |
| Course | MEDICAL RECORDS |
| Year | 1st Year |
| Semester | Unknown |
| Posted By | Mwalimu Evans Okoyo. |
| File Type | |
| Pages | 16 Pages |
| File Size | 907.22 KB |
| Views | 1577 |
| Downloads | 0 |
| Price: |
Buy Now
|
Description
This document outlines the Worcestershire Primary Care Trust's policy and procedures for archiving paper records. It describes sending paper records offsite for storage when onsite storage is limited. The key steps for archiving records offsite are to review files, remove duplicates, label boxes with content and retention dates, and use an approved offsite storage facility. Retrieval of archived records must follow specified procedures. The policy aims to properly retain necessary paper records while eliminating unnecessary storage.
Below is the document preview.
MAT 111 :DISCRETE MATHEMATICS
A set is a collection of distinct objects
44 Pages
1475 Views
0 Downloads
5.09 MB
Communication in Distributed System
In distributed systems, nodes communicate by sending messages, invoking remote procedures, sharing memory, or using sockets. These methods allow nodes to exchange data and coordinate actions, enabling effective collaboration towards common goals.
327 Pages
1735 Views
0 Downloads
5.03 MB
AN INTRODUCTION TO THE THEORY AND PRACTICEOF TRANSLATION
Fusing theory with advice and information about the practicalities of translating, Becoming a Translator is the essential resource for novice and practicing translators.
72 Pages
1779 Views
0 Downloads
706.82 KB
Web Application Basics
Web applications evolved from Web sites or Web systems. The first Web sites, created
by Tim Berners-Lee while at CERN (the European Laboratory for Particle Physics),
formed a distributed hypermedia system that enabled researchers to have access to
documents and information published by fellow researchers, directly from their computers. Documents were accessed and viewed with a piece of software called a
browser, a software application that runs on a client computer. With a browser, the user
can request documents from other computers on the network and render those documents
on the user’s display. To view a document, the user must start the browser and enter
the name of the document and the name of the host computer where it can be found.
The browser sends a request for the document to the host computer. The request is
handled by a software application called a Web server, an application usually run as a
service, or daemon, that monitors network activity on a special port, usually port 80.
The browser sends a specially formatted request for a document (Web page) to the
Web server through this network port. The Web server receives the request, locates the
document on its local file system, and sends it back to the browser; see Figure 2-1.
This Web system is a hypermedia system because the resources in the system are
linked to one another. The term Web comes from looking at the system as a set of
nodes with interconnecting links. From one viewpoint, it looks like a spider’s web.
The links provide a means to navigate the resources of the system. Most of the links
connect textual documents, but the system can be used to distribute audio, video, and
custom data as well. Links make navigation to other documents easy. The user simply
clicks a link in the document, and the browser interprets that as a request to load the
referenced document or resource in its place.
98 Pages
1884 Views
0 Downloads
1.17 MB
Introduction to NET framework
Before emergency of .NET framework, programmers used a number of tools to write programmers as depicted before
Windows GUI development: Win32 API, MFC, Visual
Basic, COM
Web development: ASP
80 Pages
1484 Views
0 Downloads
2.87 MB
VB.NET TUTORIAL
Before getting deeply into the subject we will first know how Businesses are related to
Internet, what .NET means to them and what exactly .NET is built upon. As per the product
documentation from a Business perspective, there are three phases of the Internet. The First
phase gets back to the early 1990's when Internet first came into general use and which
brought a big revolution for Businesses. In the First phase of the Internet Businesses designed
and launched their Website's and focused on the number of hits to know how many customers
were visiting their site and interested in their products, etc. The Second phase is what we are
in right now and in this phase Businesses are generating revenue through Online
Transactions. We are now moving into the Third phase of the Internet where profit is the
main priority. The focus here is to Businesses effectively communicate with their customers
and partners who are geographically isolated, participate in Digital Economy and deliver a
wide range of services. How can that be possible? The answer, with .NET
243 Pages
1415 Views
0 Downloads
3.46 MB
CMT 307:LIS 317 .NET PROGRAMMING
NET is a platform that provides a standardized
set of services. It’s just like Windows, except distributed over the Internet. It exports a common interface so that it’s programs
can be run on any system that supports .NET.
432 Pages
1659 Views
0 Downloads
9.5 MB
Matrices and Determinants
In many economic analysis, variables are assumed to be related by sets of linear equations. Matrix algebra provides a clear and concise notation for the formulation and solution of such problems, many of which
would be complicated in conventional algebraic notation. The concept of
determinant and is based on that of matrix. Hence we shall first explain a matrix.
40 Pages
1766 Views
0 Downloads
724.52 KB
INTRODUCTION TO ENVIRONMENTAL STUDIES
Environment influence and shaped our life. It is from the environment that we get food to eat,
water to drink, air to breathe and all necessities of day to day life are available from our environment. Thus it is the life support system. Hence the scope & importance of the
environment can be well understood.
54 Pages
1632 Views
0 Downloads
4.8 MB
CMT 438 :Ethical Hacking
Ethical hacking is an authorized attempt to gain unauthorized access to a computer system, application, or data using the strategies and actions of malicious attackers. This practice helps identify security vulnerabilities that can then be resolved before a malicious attacker has the opportunity to exploit them.
96 Pages
1633 Views
0 Downloads
3.56 MB